Difference between revisions of "Virtualisation with KVM and openQRM on Debian"
| Line 205: | Line 205: | ||
We now have to re-configure the VMs boot-sequence to 'local-boot'. To do this, follow the steps below: | We now have to re-configure the VMs boot-sequence to 'local-boot'. To do this, follow the steps below: | ||
| − | * | + | * Stop the VM by stopping its server object - '''Datacentre -> Server -> Select + Stop''' |
* The stop hook now halts the VM by sending a ACPI-Shutdown Signal to the VMs KVM monitor socket. Since in this stage there is now ACPI service running on the VM the stop action will "force-stop" the VM. This will result in a warning via an error event which can be ignored. | * The stop hook now halts the VM by sending a ACPI-Shutdown Signal to the VMs KVM monitor socket. Since in this stage there is now ACPI service running on the VM the stop action will "force-stop" the VM. This will result in a warning via an error event which can be ignored. | ||
| − | * | + | * In '''Plugins -> Virtualization -> KVM -> KVM VMs''' select the KVM Host and update the VM to boot 'local' |
| − | * | + | * Now start the VM again by starting its server object - '''Datacentre -> Server -> Select + Start''' |
Here a screenshot of the completed Debian installation after setting the boot-sequence of the VM to 'local' | Here a screenshot of the completed Debian installation after setting the boot-sequence of the VM to 'local' | ||
| Line 215: | Line 215: | ||
=== Install the 'openqrm-local-vm-client' === | === Install the 'openqrm-local-vm-client' === | ||
Now it is recommended to install the 'openqrm-local-vm-client' on the fresh installed system. For local-installed Virtual Machines (e.g. kvm(local VM), xen(local VM), lxc(local VM), openvz(local VM) which have access to the openQRM network the 'openqrm-local-vm-client' activates the plugin-client-boot-services to allow further management functionality (e.g. application deployment with Puppet, system statistics with Collectd etc). Monitoring and openQRM actions are still running on behalf of the VM Host. | Now it is recommended to install the 'openqrm-local-vm-client' on the fresh installed system. For local-installed Virtual Machines (e.g. kvm(local VM), xen(local VM), lxc(local VM), openvz(local VM) which have access to the openQRM network the 'openqrm-local-vm-client' activates the plugin-client-boot-services to allow further management functionality (e.g. application deployment with Puppet, system statistics with Collectd etc). Monitoring and openQRM actions are still running on behalf of the VM Host. | ||
| − | |||
| − | |||
The 'openqrm-local-vm-client' also automatically makes sure that the 'acpi-support/acpid' package is installed to enable the reboot/restart functionalities of KVM via the VM monitor socket. To install the 'openqrm-local-vm-client' on VM, follow the steps below: | The 'openqrm-local-vm-client' also automatically makes sure that the 'acpi-support/acpid' package is installed to enable the reboot/restart functionalities of KVM via the VM monitor socket. To install the 'openqrm-local-vm-client' on VM, follow the steps below: | ||
| Line 241: | Line 239: | ||
'''Congratulations!''' | '''Congratulations!''' | ||
| − | You have completed this openQRM How-To | + | You have successfully completed this openQRM How-To! |
Latest revision as of 10:34, 10 December 2020
This How-To explains how to create and manage KVM Virtual Machines on Debian with openQRM
Requirements
- One physical Server
- at least 1 GB of Memory
- at least 100 GB of Diskspace
- VT (Virtualization Technology) enabled in the Systems BIOS so that the openQRM Server can run KVM Virtual Machines later
- A minimal Debian installation on a physical Server
- openQRM installed
NOTE:
For this How-To, we assume you have successfully installed openQRM and have at least referenced our Cloud Computing with openQRM on Debian How-To before. If not, it is highly suggested to complete both before continuing
Set a custom Domain name
As the first step after the openQRM installation and initialization it is recommended to configure a custom domain name for the openQRM management network.
In this Use-Case, the openQRM Server has the private Class C IP address 192.168.178.5/255.255.255.0 based on the install openQRM on Debian How-To. Since the openQRM management network is a private one any syntactically correct domain name can be used e.g. 'my123cloud.net'.
The default domain name pre-configured in the DNS plugin is "oqnet.org".
Best practice is to use the 'openqrm' command line util to setup the domain name for the DNS plugin. Login to the openQRM Server system and run the following command as 'root' in a terminal:
/usr/share/openqrm/bin/openqrm boot-service configure -n dns -a default -k OPENQRM_SERVER_DOMAIN -v my123cloud.net
The output of the above command will look like
root@debian:~# /usr/share/openqrm/bin/openqrm boot-service configure -n dns -a default -k OPENQRM_SERVER_DOMAIN -v my123cloud.net
Setting up default Boot-Service Configuration of plugin dns
root@debian:~#
To review the current configuration of the DNS plugin run:
/usr/share/openqrm/bin/openqrm boot-service view -n dns -a default
Enabling Plugins
In the openQRM Plugin Manager, enable and start the following plugins in the sequence below:
- dns plugin - type Networking
- dhcpd plugin - type Networking
- tftpd plugin - type Networking
- network-manager plugin - type Networking
- local-server plugin - type Misc
- device-manager plugin - type Management
- novnc plugin - type Management
- sshterm plugin - type Management
- linuxcoe plugin - type Deployment
- kvm plugin - type Virtualization
Create the Virtualization Host Object
Go to Datacenter -> Server -> Add a new Server
Enter 'openqrm' as the server name and provide a descriptive description
Select the openQRM Server resource
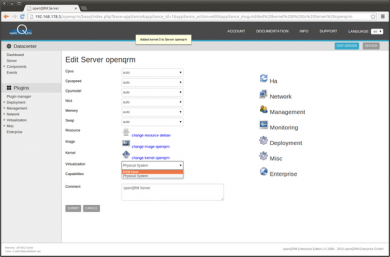
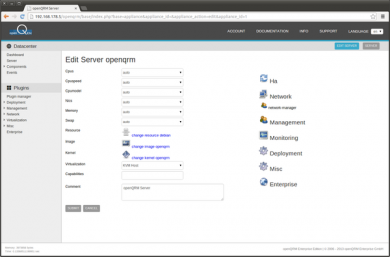
In the following Edit dialog, set 'KVM Host' as the Virtualization type of this server, then submit to save
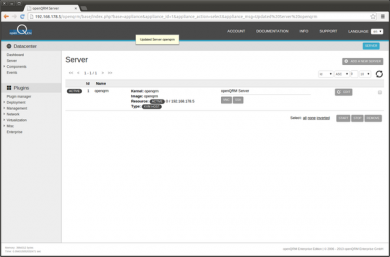
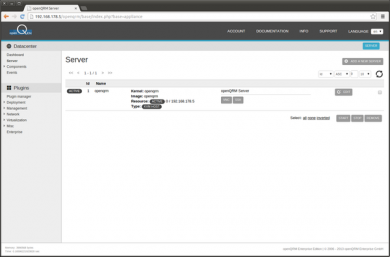
This is the Server list after adding the Virtualization Host Object.
Additionally 2 KVM Storage Objects are automatically created to manage different types of VM volumes
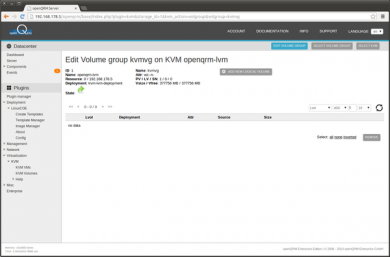
Create a LVM Volume Group
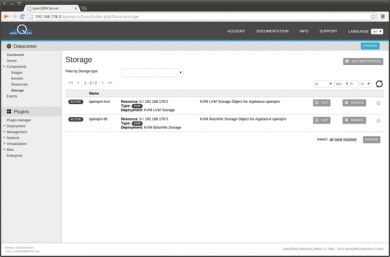
The KVM Storage type with the best flexibility regarding volume management is 'KVM LVM Storage'. Each VM gets its own dedicated logical volume as its root image. Alternatively 'KVM Blockfile Storage' can be used. Volumes for this storage type are created on the Hosts filesystem via the qemu-img command. This How-To describes the 'KVM LVM Storage' type.
Go to Datacenter -> Storage and click on the 'manage' button of the 'openqrm-lvm' storage object
NOTE:
The system automatically checks if the system utilities for the LVM functionalities are available. If not it openQRM triggers to automatically install them via the distribution package manager. This may delay the first time the command is executed on the system.
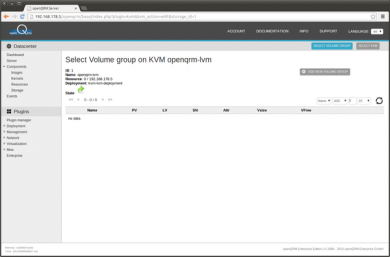
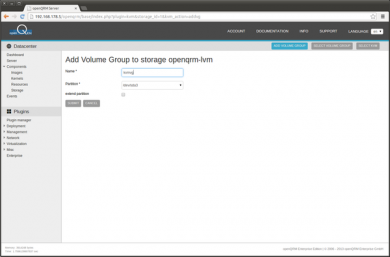
Now click on 'Add new Volume group'
When you have followed the initial 'How-To install openQRM 5.1 on Debian Wheezy' How-To, there is now a dedicated /dev/sda3 partition available which can be used to create a LVM Volume group. Provide a name for the LVM Volume group (here 'kvmvg'), select the /dev/sda3 device and submit.
Confirm to create the new Volume group
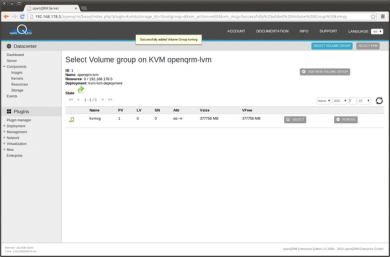
The LVM Volume group to store the VM Images is created now
Create one or more network bridges
The KVM Virtualization technology uses network bridges to connect the Virtual Machines virtualised network interfaces to real networks.
Go to Datacentre -> Server and click on 'Edit' of the openQRM server object
In the server edit section select Network -> Network Manager.
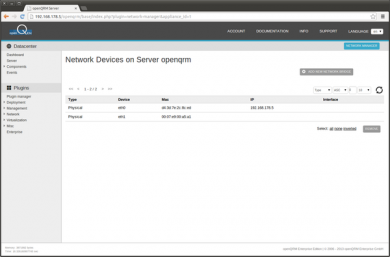
This will provide a list of all available network interfaces on the system
NOTE:
The system automatically checks if the system utilities for the bridge and network functionalities are available. If not, openQRM triggers to automatically install them via the distribution package manager. This may delay the first time the command is executed on the system.
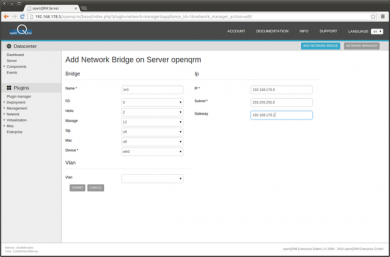
Click on 'Add new network bridge' to create a new network bridge
Fill in 'br0' as the bridge name, select eth0 (the openQRM Management network interface) and insert the same IP configuration as for eth0. In this How-To, the IP 192.168.178.5/255.255.255.0 is used with a default gateway 192.168.178.1. Then click on submit to create the new network bridge.
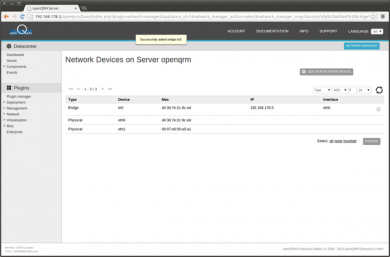
Here a screenshot of the network interface list after creating the new network bridge 'br0'.
Create a LinuxCOE automatic-installation template
The LinuxCOE Project provides a useful UI to create automatic-installation ISO images for various Linux distribution e.g. preseed, kickstart and autoyast. Those ISO images can be then used to fully automatically install a Linux distribution without any manual interaction needed.
The integration of LinuxCOE in openQRM makes those automatic-installation ISO images automatically available on all Virtualization Hosts (mounted by nfs at /linuxcoe from the openQRM server). This makes it easy to configure a Virtual Machines installation boot image from the central ISO Pool mount point.
NOTE:
The LinuxCOE plugin in openQRM comes with a fully automatically setup and pre-configuration of LinuxCOE. Since LinuxCOE is an installation-framework it is recommended to add further custom configuration such as local package mirrors, new distribution data and config files etc. Read more about how to further enhance your LinuxCOE installation at http://linuxcoe.sourceforge.net/#documentation
First step is to create a new automatic-installation profile and ISO image.
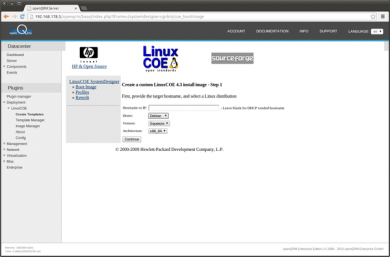
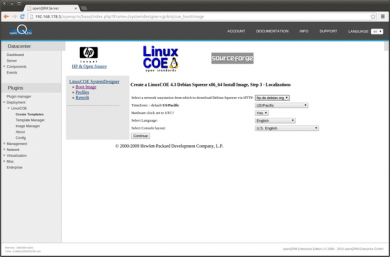
Go to Plugins -> Deployment -> LinuxCOE -> Create Templates and select a Linux distribution and version for the automatic-installation. For this How-To we will use 'Debian Squeeze 64bit'. Leave the hostname input empty since openQRM will care about this via its dhcpd plugin.
Leave the default settings on the next page of LinuxCOE wizard.
Next, select a Mirror from the list.
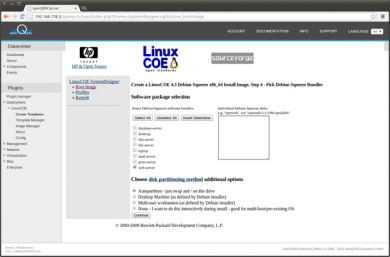
Here, provide your custom package setup for the automatic-installation.
On the following page leave the default settings
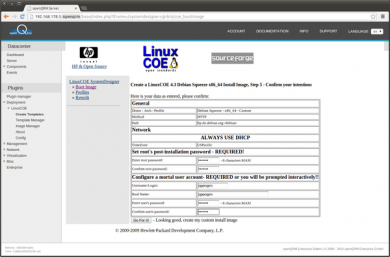
The summary page of the LinuxCOE wizard allows to preconfigure a root and user account. Click on 'Go for it' to create the automatic-installation template.
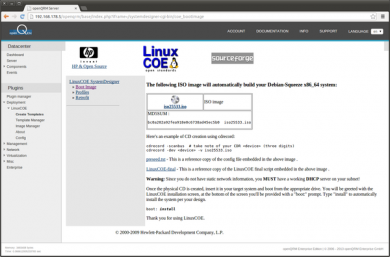
The ISO image is created. No need to download it since it will be used for a KVM Virtual Machine installation on the openQRM server.
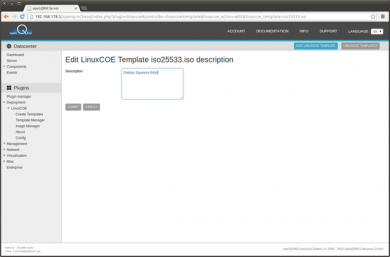
Go to Plugins -> Deployment -> LinuxCOE -> Template Manager and click on 'Edit'.
Now provide a description for the just created automatic-installation template.
Here the list view of the updated automatic-installation template.
Create a new KVM Virtual Machine
Use openQRM's Server Wizard to add a new KVM Virtual Machine. This Wizard works in the same way for physical systems, KVM VMs, Xen VMs, Citrix XenServer VMs, VMware VMs, LXC VMs and openVZ VMs.
Go to Datacenter -> Server -> Add a new Server
Give a name for the new server. Easiest is to use the 'generate name' button. Also provide a useful description.
In the Resource-Selection, click on 'new resource'. A resource in openQRM is a logical generic object which is mapped to a physical system or Virtual Machine of any type.
On the next page find a selection of different resource types to create. Choose 'KVM (localboot) Virtual Machine'
This forwards to the KVM Host selection. Select the openQRM server for the Virtualization Host of the VM to create
On the KVM Virtual Machine Overview click on 'Add local VM'
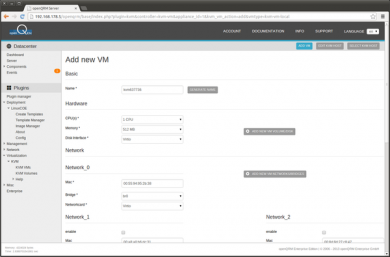
In the VM add form provide a name for the new VM. Again the easiest is to use the 'generate name' button. There are lots of different parameters which can be configured. Anyway you can go with most of the default selection. Just make sure the first network card of the VM is connected to the previously created bridge 'br0'
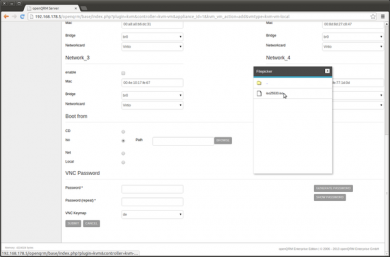
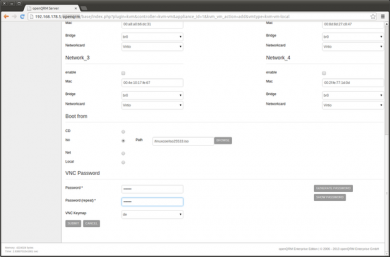
Further down the VM add form, configure the boot sequence of the VM. Select 'iso' and open the Filepicker by clicking on the 'Browse' button. This will open a small new window listing the filesystem of the Virtualization Host. Navigate to '/linuxcoe' and select the previously created LinuxCOE automatic-installation iso image. Not that the name of the iso image may be different in your setup.
Also do not forget to set a VNC password to be able to connect to the VM console later. Then click on 'Submit'
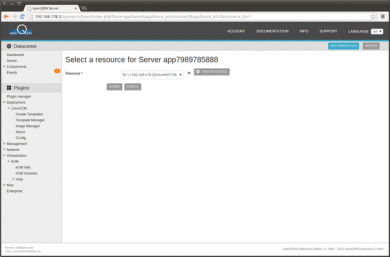
Creating the new VM automatically forwards back into the server wizard with the new created resource available. Select the new resource and 'Submit'
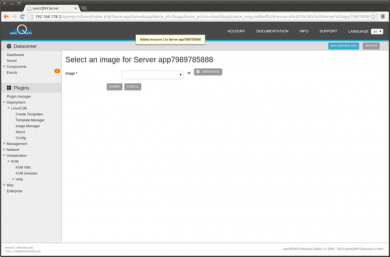
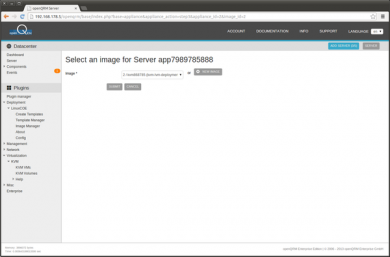
We haven't created an Image for the Virtual Machine yet. An Image in openQRM is a logical and generic object which is mapped to the physical volumes of different storage types. So click on 'New Image'
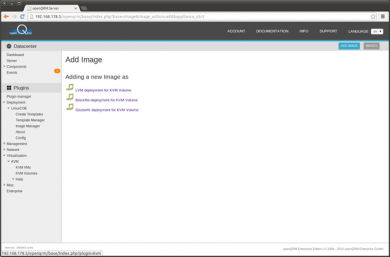
Adding a new Image forwards to the Image type selection. Select 'LVM deployment for KVM volume'
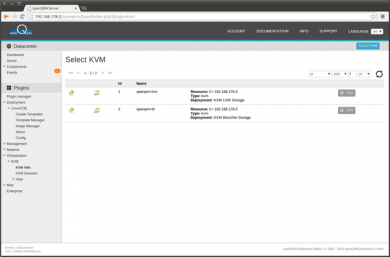
In the storage server selection, select the 'openqrm-lvm' storage object
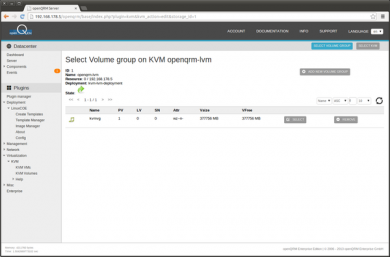
Then select the 'kvmvg' LVM volume group
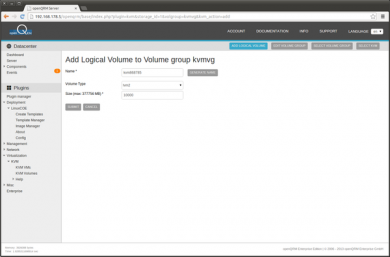
In the LVM volume overview click on 'Add new logical volume'
Provide a name and size (in MB) for the new volume. Again the easiest is to use the 'generate name' button. Then 'Submit'
Creating the new Image automatically forwards back into the server wizard with the new created image available. Select the new image and 'Submit'
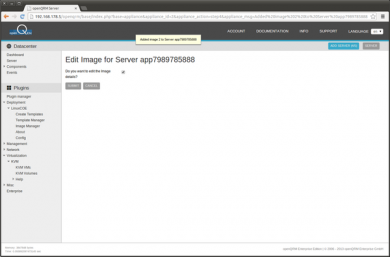
Click on 'Submit' to edit the Image parameter
This following step allows to edit further Image parameters e.g. setting a root password
The last step in the server wizard presents the full configuration and allows to further setup network, management, monitoring and deployment configuration. Click on 'Submit' to save the server configuration.
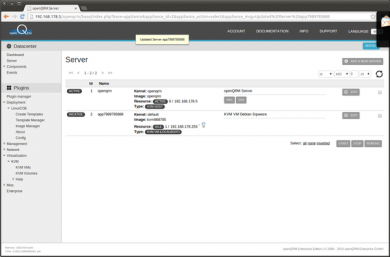
The server overview list the new server, not yet activated. Select the new created server and click on 'Start'
Confirm starting the server
Started the new server, now marked as 'active'. Starting the logical server object triggers to actually start the resource (the KVM VM) with the configured Image (the LVM volume) and triggers additional automatic configuration tasks via a plugin-hook. This server start and stop hooks are checking each activated plugin if there is work to do. For a few examples how hooks are used in openQRM check the list below:
- The DNS plugin is using those hooks to automatically add (or remove) the server name into the managed bind server
- The Dhcpd plugin add the "hostname option" for the server to its configuration
- The Nagios plugin adds/removes service checks for automatic monitoring
- The Puppet plugin activates configured application recipes to automatically setup and pre-configure services on the VM
Go to Plugins -> Virtualization -> KVM -> KVM VMs and select the openQRM server. In the KVM VM overview click on the 'console' button of the VM. This opens a VNC console within your web browser
NOTE: You need to deactivate the browsers Pop-up Blocker for the openQRM website!
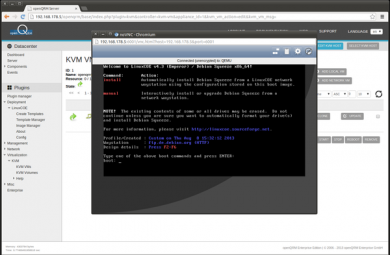
To start the automatic installation, type 'install' in the VNC console and press ENTER.
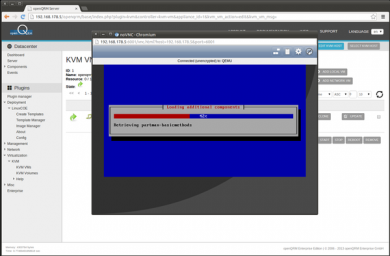
The KVM VM is now automatically installing a Debian Linux distribution. This may take a while
NOTE: After the automatic installation via the attached LinuxCOE ISO image the VM reboots to the install screen again.
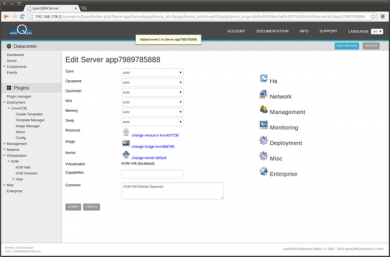
We now have to re-configure the VMs boot-sequence to 'local-boot'. To do this, follow the steps below:
- Stop the VM by stopping its server object - Datacentre -> Server -> Select + Stop
- The stop hook now halts the VM by sending a ACPI-Shutdown Signal to the VMs KVM monitor socket. Since in this stage there is now ACPI service running on the VM the stop action will "force-stop" the VM. This will result in a warning via an error event which can be ignored.
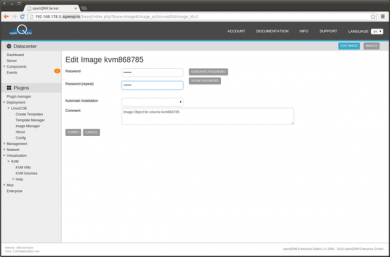
- In Plugins -> Virtualization -> KVM -> KVM VMs select the KVM Host and update the VM to boot 'local'
- Now start the VM again by starting its server object - Datacentre -> Server -> Select + Start
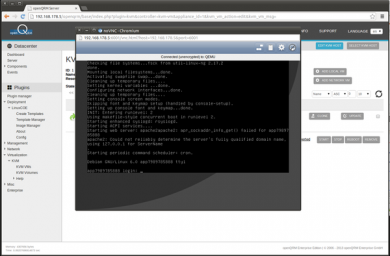
Here a screenshot of the completed Debian installation after setting the boot-sequence of the VM to 'local'
Install the 'openqrm-local-vm-client'
Now it is recommended to install the 'openqrm-local-vm-client' on the fresh installed system. For local-installed Virtual Machines (e.g. kvm(local VM), xen(local VM), lxc(local VM), openvz(local VM) which have access to the openQRM network the 'openqrm-local-vm-client' activates the plugin-client-boot-services to allow further management functionality (e.g. application deployment with Puppet, system statistics with Collectd etc). Monitoring and openQRM actions are still running on behalf of the VM Host.
The 'openqrm-local-vm-client' also automatically makes sure that the 'acpi-support/acpid' package is installed to enable the reboot/restart functionalities of KVM via the VM monitor socket. To install the 'openqrm-local-vm-client' on VM, follow the steps below:
Copy the 'openqrm-local-vm-client' utility to the running VM
scp openqrm-local-vm-client [ip-address-of-the-VM]:/tmp/
Then login to the VM
ssh [ip-address-of-the-VM]
This prompts for the password which was configured in the LinuxCOE automatic-installation template. Give the password and execute the openqrm-local-vm-client utility
/tmp/openqrm-local-vm-client
This will automatically setup the 'openqrm-local-vm-client' in the system init and start it.
Create additional KVM VMs by cloning/snapshotting the Volume
Go to Plugins -> Virtualization -> KVM -> KVM Volumes and select the 'openqrm-lvm' storage object. Then choose the 'kvmvg' logical volume group to get a list of all available LVM volumes.
In this view you can use the 'clone' or 'snap' action to clone or snapshot existing, installed KVM LVM Volumes. The 'clone' action creates a new logical volume and copies the content of the origin over. Snapshotting is using the "copy-on-write" mechanism of LVM which is much more efficient. Actually, a deployed snapshot of a KVM LVM Volume just stores the changes compared to its origin. That means that creating snapshots e.g. per user allows to 'just' store the data which is different per user.
Congratulations!
You have successfully completed this openQRM How-To!