Fully Automatic OpenStack Cloud Installation on Bare Metal with openQRM
This How-To is about how to fully automate provisioning of OpenStack Cloud(s) to bare-metal systems (physical server) with openQRM.
Why do we integrate with e.g. Amazon EC2, Eucalyptus and OpenStack (and some more in the pipeline)?
Pure Cloud projects normally only care for virtual machine deployment. That means the Cloud is actually something within your datacentre so it needs management and administration in the same way as regular IT.
Since openQRM Enterprise works on a much lower level of your IT, we see other Cloud providers as tools. Because of this, those tools need a comprehensive management platform to automate them to 100%. Therefore, in openQRM, public and private Cloud providers are basically just another resource type and we are happy to integrate with them.
Requirements
- One (or more) physical Server
- at least 1 GB of Memory
- at least 100 GB of Diskspace
- VT (Virtualization Technology) enabled in the Systems BIOS so that the openQRM Server can run Virtual Machines later
- Debian Installation on a physical Server
Note:
OpenStack installation to bare-metal is only available in the openQRM Enterprise Edition >= 5.1.3.
For this How-To, we assume you have successfully installed openQRM and have at least referenced our Cloud Computing with openQRM on Debian How-To before. If not, it is highly suggested to complete both before continuing.
For demonstration, we are going ot be using the openQRM server used for the 'Virtualisation with KVM and openQRM on Debian' and 'Automated Amazon EC2 Cloud deployments with openQRM on Debian' How-Tos.
1. Enable plugins
In the openQRM Plugin Manager please enable and start the following plugins in the sequence below:
- dns plugin - type Networking
- dhcpd plugin - type Networking
- tftpd plugin - type Networking
- network-manager plugin - type Networking
- local-server plugin - type Misc
- device-manager plugin - type Management
- novnc plugin - type Management
- sshterm plugin - type Management
- linuxcoe plugin - type Deployment
- puppet plugin - type Deployment
Hint: You can use the filter in the plugin list to find plugins by their type easily!
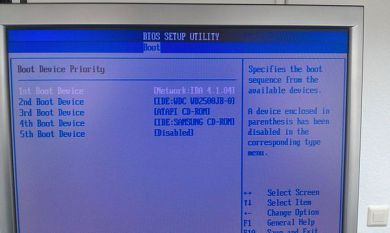
2. Enable PXE boot on the second system dedicated for OpenStack
Set the second system dedicated for OpenStack to the following boot-sequence in the system bios:
- network-boot (PXE)
- boot from first hard drive
- disabled
3. Save the bios settings and reboot
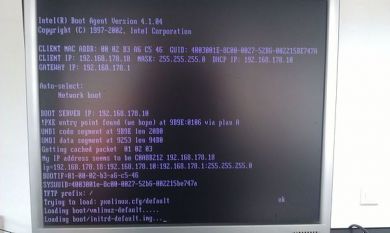
After the reboot the system now boots directly from the network-boot environment (dhcpd/tftp/pxe) by openQRM and integrates itself as new, "idle" (not in used) resource.
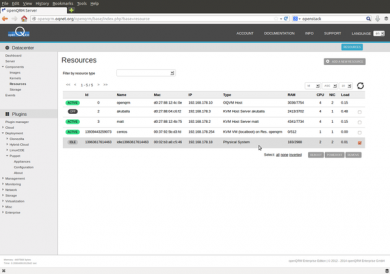
Here the new resource in "idle" state. Idle means that the system is integrated and ready to be automatically managed by openQRM.
4. Setup an automatic-installation profile with LinuxCOE
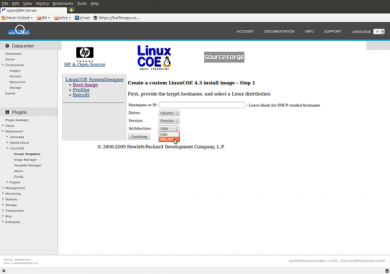
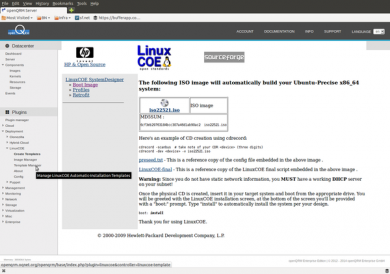
Go to Plugins -> Deployment -> LinuxCOE -> Create Templates and select Ubuntu "Precise" (12.04 LTS) as the distribution version and X86_64 as the architecture. Then click on "continue".
on the next page, leave settings on default and simply click on "continue"
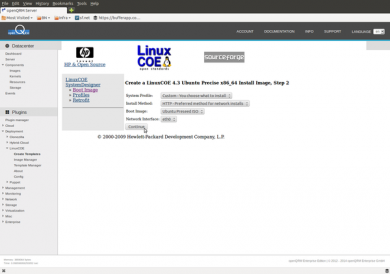
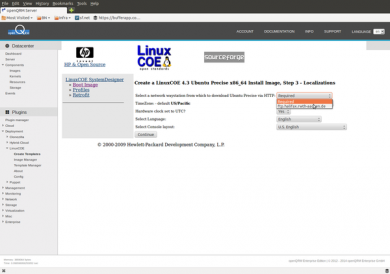
On the following page select the mirror from where you would like to install.
Please notice that you can add your own custom mirror entries in the LinuxCOE configuration easily at /usr/share/openqrm/plugins/linuxcoe/linuxcoe-sd/depots/apt-Ubuntu-Precise
In the package selection please select only "openssh-server"
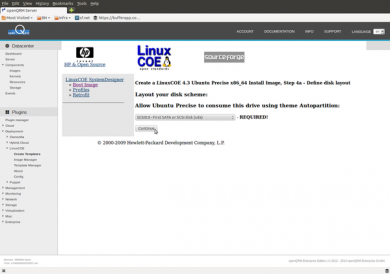
In the disk-layout screen please select /dev/sda
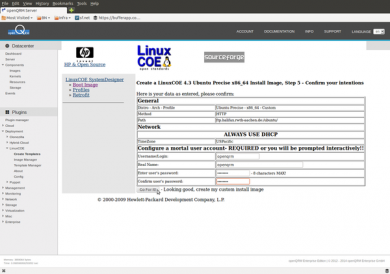
In the user configuration section please specify a username and password
The final LinuxCOE page presents the ready-baked iso image containing the automatic installation. No need to download it as openQRM is going to apply this automatic-installation profile by PXE/network-boot!
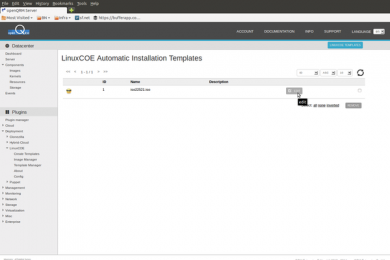
Instead, go to Plugins -> Deployment -> LinuxCOE -> Template Manager
which will automatically unpack the iso and its configuration items.
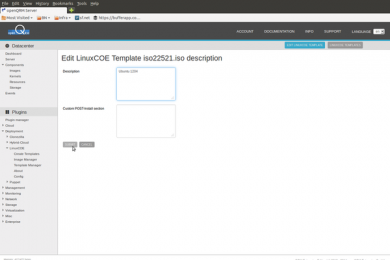
Please click on the "edit" action of the installation-template
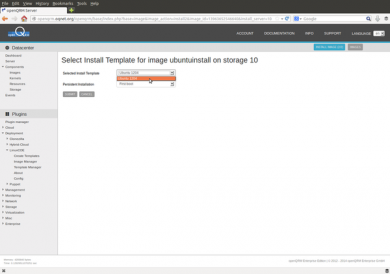
Now insert "Ubuntu 1204" as the installation-template name and click on "submit".
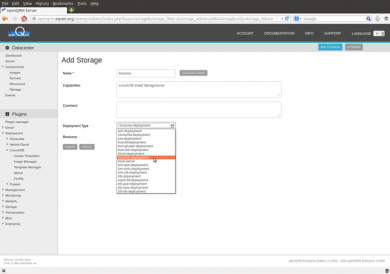
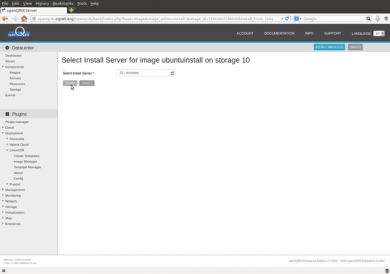
Next please go to Datacentre -> Components -> Storage -> Add Storage and add a new storage from the type "linuxcoe-deployment". Use the openQRM server resource for this new storage object.
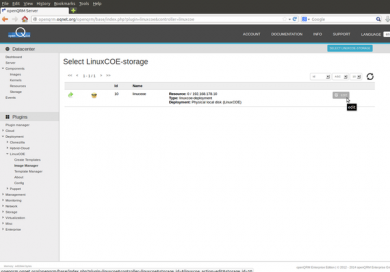
Switch back to Plugins -> Deployment -> LinuxCOE -> Image Manager and select the just created new LinuxCOE Storage.
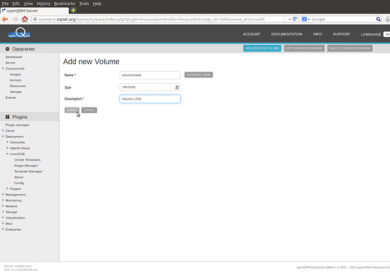
Click on "Add new Volume"
Name the new volume "ubuntuinstall", select /dev/sda and add "Ubuntu 1204" as the description. This will create the Image pointing to the target harddisk on the system which is going to be auto-installed.
Adding the volume automatically adds a new Image object in openQRM.
5. Creating a new server with an attached automatic installation-template
We now have all configuration items ready for the deployment.
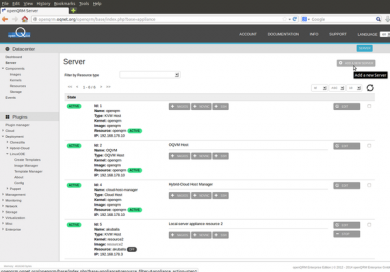
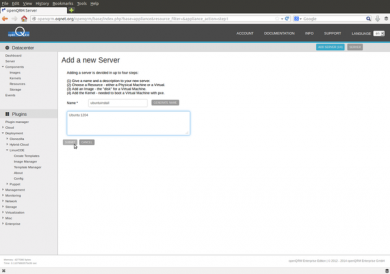
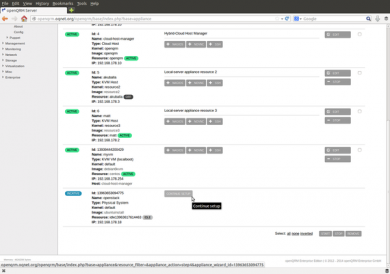
Please go to Datacentre -> Server and click on "Add new server"
Enter "openstack" as the name and "Ubuntu 1204" as the description. Then click on "submit".
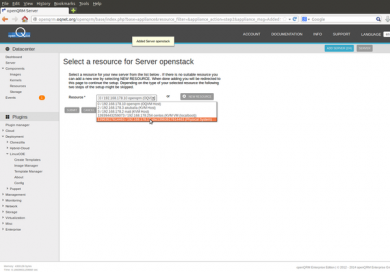
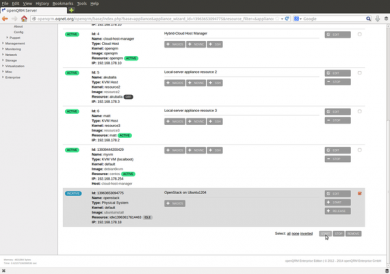
On the second page of the server wizard please select the resource of the just integrated, idle, bare-metal system dedicated for the OpenStack installation.
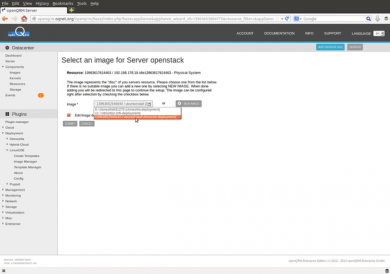
On the third page of the server wizard, select the just created "ubuntuinstall" LinuxCOE-deployment Image, enable the "Edit Image" checkbox and click on "submit".
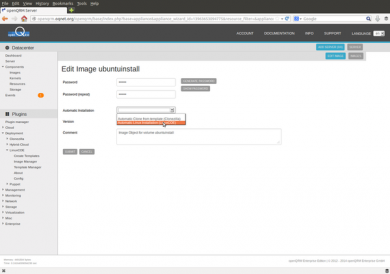
In the Image-Edit section please now attach the LinuxCOE installation-template to the Image. Optional you can reset the system password from the automatic installation by setting a custom one.
Now select the LinuxCOE storage
On the next screen, select the "Ubuntu 1204" installation-template which is then attached to the Image. Please also make sure that the persistent installation is set to "first boot only".
In the server list now please choose "continue setup" for the server OpenStack.
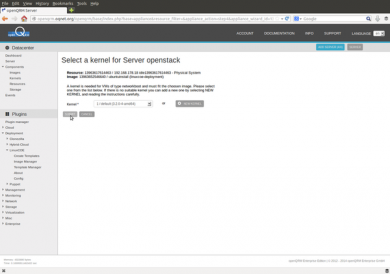
Back in the server wizard please select the "default" kernel for the server OpenStack.
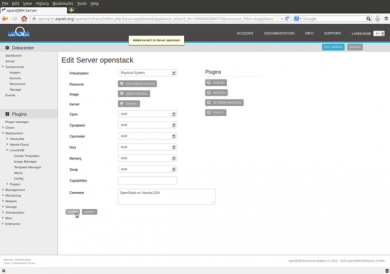
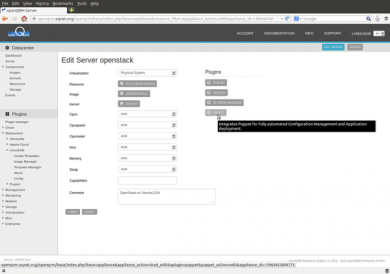
The server object is created so far. Here the Server-Edit section, the final screen of the wizard. Here we can now attach the Puppet recipe for the automated OpenStack installation on top of our automated operating system installation.
In the Server-Edit section please set your custom parameters for the automatic OpenStack installation in the server "capabilities" field. The parameters are the same as user by DevStack.
For example, for this How-To we have used the following server capabilities configuration (all parameter in one line):
HOST_IP=193.168.88.135 FLOATING_RANGE=193.168.88.0/27 FIXED_RANGE=10.20.11.0/24 FLAT_INTERFACE=eth0 ADMIN_PASSWORD=password MYSQL_PASSWORD=password RABBIT_PASSWORD=password SERVICE_PASSWORD=password SERVICE_TOKEN=password
After setting the OpenStack configuration parameters in the server capabilities field please click on "submit" to save your changes. The go back to the Edit-Server screen and click on the Puppet item.
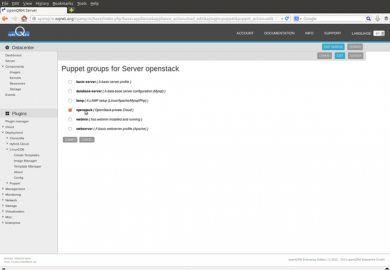
In the Puppet configuration for the server OpenStack please select the "OpenStack" recipe and click on "submit".
6. Starting the server
Navigate to the Server-List at Datacenter -> Server, select and start the server 'openstack'.
Starting the server object now automatically:
- assigns the LinuxCOE installation-template to the server on first boot
- triggers all other start actions of the server
- reboots the "idle" server resource
- PXE boots the resource assigned to LinuxCOE
- automatic installs the OS on the systems hard disk
- re-assigns the system to local-boot
- after the successful OS installation it reboots the system which then boots from the local disk
- install and start the openQRM-Client (comparable to the "cloud-init" scripts for Amazon EC2 or OpenStack) on the installed system
- by starting the openqrm-client the system automatically fetches the plugin-boot-services from the openQRM server
- the Puppet-boot-service then automatically installs Puppet on the system and runs the configured OpenStack-installation recipe.
Congratulations!
You have successfully completed this How-To!